How Did I Get Here?

Networks are complex; even the simple ones can be. There are lots of reasons for this. For one it is just mind boggling how much engineering has to go into even the simplest network device. It would take an entire book just to describe in detail how a Raspberry PI works including the circuit diagrams, components, microcode, interfaces and a PI is practically a trinket in computer complexity. Beyond the complexity of the devices though is the number of paths that lead onto the network. Sure, you've got some RJ45/Cat5 connections and WIFI (probably a lot of WIFI) but lets not forget the random switch or router laying around that probably has some ports. And about that WIFI... how many networks do you have on WIFI? Usually there are at least 2 different radios available, 5ghz and 2.4ghz, and those are available to who? Employees? Customers? Do you have an "open" customer WIFI?
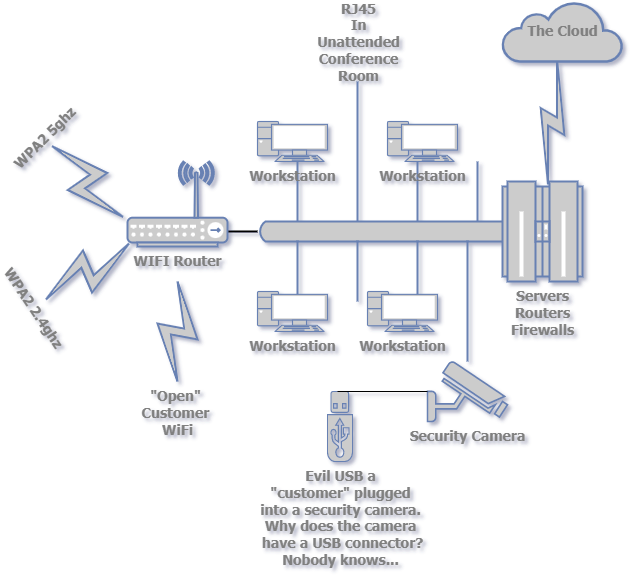
This is what I call, "The Scary Network Diagram" its a conversation starter I use when talking to new customers about how things can get into a customer network on purpose, on accident, and "on accident". These days everyone is focused on the Internet as an attack vector and they should be. But the attack surface of your organization includes even more. This is a simple diagram, it probably adequately describes the network at the auto shop I take my cars too. But while the networks get bigger, the base principals can remain the same.
Asset Inventory
For the purposes of securing a network one of the 1st steps has to be, what is connected to the network? Looking at my diagram we see some workstations, security cameras, WIFI and a connection to the Internet "Cloud". If possible it would be best if nothing got on the network that wasn't specifically authorized by management. It is possible to use rules at the infrastructure level (router and firewall) to try to accomplish this, it won't be perfect but is definitely a step your network admins should take if feasible. Most of the time though we need some flexibility in what gets on the network.
Most would do that by segmenting the network into various levels of trust. At a simple level, based on the diagram the workstations physically plugged into the network might have a high level of trust. We put the workstations there, highered the people sitting by them, and (should) realize if someone else were there. Of course we don't trust them implicitly, just that we trust them more than others.
Speaking of others... the WIFI users....You've probably implemented WPA2 or some similar security on your WIFI network. So your users have to enter a, hopefully, complex password to gain access. But they are probably using their own laptops and phones to do that and who knows where those things have been or what is on them. Also a disgruntled or easily influenced person with the password could pass it along to non-authorized users. So the WIFI network should probably not be at the same level of trust as the workstations.
Of course at the absolute bottom of the pile is any "unsecured" connection. So "customer" WIFI connections, whether passworded or not, should not be trusted at all. So goes unsecured devices like that camera in the diagram. Both of those access points also share a common trait: neither has any need to access corporate resources.
So what we have in very simple terms is 3 levels of network security:
- Highly trusted because its highly controlled;
- Sort of trusted because we have some control;
- Not trusted at all because we have no control.
Breaking In
As an attacker I'm 1st going to look for low hanging fruit. This is nothing different than a burglar would do: go for the easily opened window instead of through the locked steel door. If I'm attacking you from a distance then I'll come in through your Internet connection which hopefully is not trusted at all until something is done to secure it like a private VPN (Virtual Private Network).
If I'm local I have several other paths to compromise your systems. I could pose as a customer and look for a place to stick a USB "rubber ducky" (a very naughty device) where it shouldn't go. Maybe posing as a potential customer I could get a briefing by a sales person in the conference room with an open Ethernet RJ45 jack. If I'm left alone for a few minutes I will leave behind a Raspberry PI attached to it giving me access to whatever is on that network. You see that even among the "hardline" interfaces there is a differentiation of trust. Authorized workstations plugged into an RJ45 jack are trusted; RJ45 jacks in conference rooms, waiting rooms, exam rooms...basically any place where bad people can act without direct observation just can't have a high level of trust.
I will have carried in with me a sniffer to capture WIFI packets. Those packets will go home with me where I can try to crack your WIFI password on a special rig I have just for that. If your passwords lack complexity then there is a good chance I'll eventually crack them.
But why do all that when there is an "open" WIFI connection available to customers? Is that secure?
That is just the situation that inspired this blog post. I was at a branch of a nationwide company and talking with the manager who had just taken over from the previous person. He was explaining the network as it had been explained to him. The 5gh WIFI was reserved for managers, the 2.4ghz for employees with phones, and the "open" WIFI was for customers. All of them were isolated from each other, he told me. Because its just how I am, I connected to the "open" WIFI on my phone and ran an ARP listener. I stopped counting at over 100 devices it found on this "isolated" network. I showed the list that had the device names from their MAC addresses on it to the manager. He identified his cash registers, manager workstations, lights, cameras, everything. It was all accessible.
I'm a good guy. I didn't do anything else other than tell him the problem and hope his company would fix it, but if I wasn't what a disaster it could be.
Networks evolve over time. Even if they were setup with security in mind that might have changed. As the saying goes, "needs must when the devil drives." As requirements have changed, emergencies happened, or even just the natural changes imposed by technological upgrades, your network may need a security checkup. It would be best if someone like me did it rather than a bad guy.
Good news, we have time in our schedule coming up!
Learn more about our internal or "assumed compromise" test today. Our certified pentesters will analyze your network to provide detailed analysis and reporting you can use to further secure your network.
Author
Kirby Angell is the CTO of Alertra, Inc. and a certified pentester. In addition he has written several articles on Python programming for magazines back when that was a thing. He contributed a chapter to the 1st edition of "The Quick Python Book" published by Manning. He was one of the first 10 Microsoft Certified Solution Developers. Ah the 90s...he probably still has a "Members Only" jacket. He is certified to teach firearms classes in Oklahoma and holds a black belt in mixed martial arts.

Archives:
- April 2022 (1)
- April 2021 (1)
- February 2021 (1)
- January 2021 (2)
- December 2020 (1)
- January 2020 (2)
- October 2019 (1)
- September 2019 (1)
- August 2019 (1)
- July 2019 (1)